stride model in security testing – microsoft stride chart
system component risks the entire system security The paper identifies that STRIDE is a light-weight and effective threat modeling methodology for CPS that simplifies the task for security analysts to identify vulnerabilities and plan appropriate component level security measures at the system design stage,
Finding security defects early in the SDLC with STRIDE
· Once each aspect of the STRIDE model is discussed and the potential vulnerabilities captured each should either be remediated or determined to be acceptable risks A brief scenario of the threat model As an example the STRIDE model can be used as a threat modeling approach for …
How Threat Modeling Can Influence ICS Security Posture
· Fichier PDF
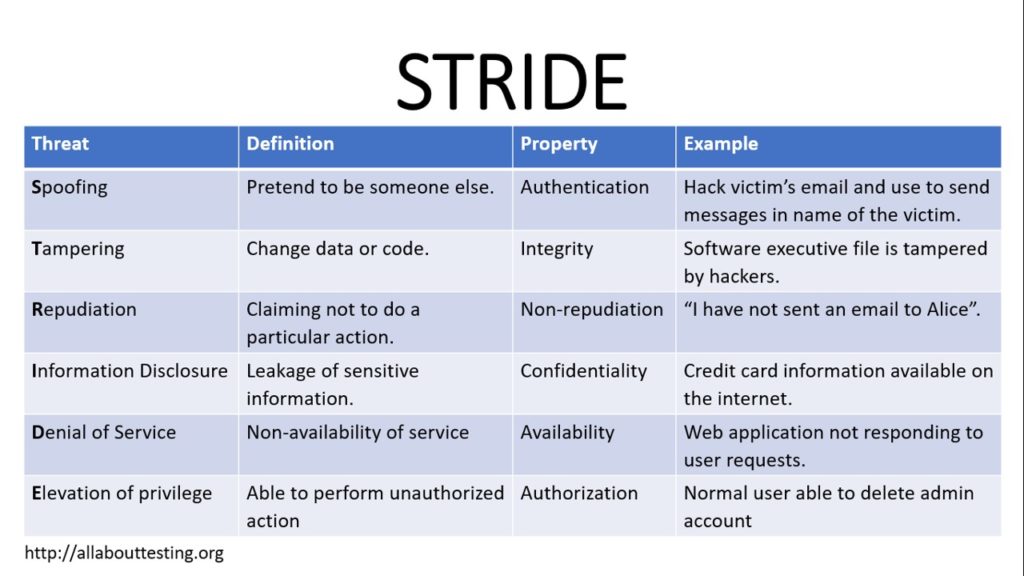
STRIDE: Acronym of Threat Modeling System
· Besides Bedi et al 2013 employed STRIDE model spoofing identity tampering with data repudiation information disclosure denial of service, and elevation of privilege, and enumerated the asset threatened in a table, It is also clear to see from Table 4 that, threat modeling methods can …
Threat Modeling: 12 Available Methods
· STRIDE and Associated Derivations Invented in 1999 and adopted by Microsoft in 2002 STRIDE is currently the most mature threat-modeling method STRIDE has evolved over time to include new threat-specific tables and the variants STRIDE-per-Element and STRIDE-per-Interaction STRIDE evaluates the system detail design It models the in-place system
Manquant :
security testing
STRIDE-based Threat Modeling for Cyber-Physical Systems
· Fichier PDF
· In this article, we will take a look at one of the popular threat modeling methodology known as STRIDE, Praerit Garg and Loren Kohnfelder developed STRIDE at Microsoft in 1999, STRIDE stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege, STRIDE threats are against some security properties like Authentication, Integrity, Non-repudiation, Confidentiality, …
Temps de Lecture Estimé: 6 mins
Uncover Security Design Flaws Using The STRIDE Approach
STRIDE • Invented in 1999 & Adopted by Microsoft in 2002 • The most mature • It evaluates the system architecture by using Data Flow Diagrams DFD • It is used to identify system’s entities and boundaries • It applies a general set of known threats based on its acronym …
A Beginners Guide to the STRIDE Security Threat Model
Spoofing
· Once you get used to applying the STRIDE model it often boils down to getting the DFD right brainstorming attacks and reviewing the known checklists This can go pretty quickly As you strive to develop secure software we recommend threat modeling as a key part of your process, and specifically the STRIDE model presented in this article, But the key point is to find a method that works for you, apply it early in your …
Security Testing
· STRIDE: Acronym of Threat Modeling System, by AAT Team, Updated February 21, 2019, Today we will discuss STRIDE, It is an acronym for threat modeling system, It helps to classify security attacks among six different threat types, In simple terms, any cyber attack can be classified among STRIDE, It is defined as:
Without STRIDE the DREAD model also can be used in assessing analyzing and finding the risk probability by
Threat modeling – A systematic literature review
STRIDE-Threat Modeling Technique
stride model in security testing
Threat modelling and stride
One methodology for threat modelling is STRIDE, The STRIDE methodology was created by Microsoft and is a mnemonic device to assist in remembering six particular areas of threat: Spoofing is the creation of fake data, or the theft and re-use of authentication credentials, Tampering …
PDF Risk-driven security testing using risk analysis
Threat modeling approach STRIDE is generally used to identify both technical and non-technical threats present in the system Thus a security testing mechanism based on risk analysis results
For all-inclusive security testing service, you should partner with Stridely Solutions, Starting from detailed analysis and evolution of your IT infrastructure to create application exposure layers, we offer every bit of it, Our security testing consultant goes to extra miles to make sure that all of your software, systems, and web/mobile applications are not under any kind of cyber threat and functioning without any hassles,